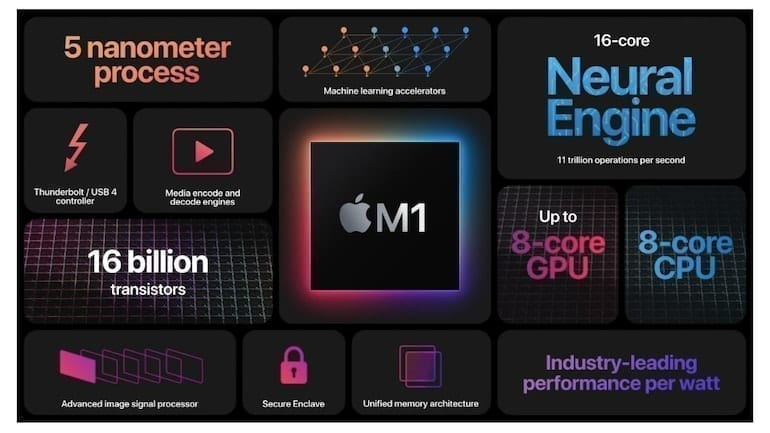
Apple M1 Transition Testing
Back in February we discussed the changing CPU landscape that was occurring within the industry. We specifically covered the shift towards ARM-based RISC processors such as Qualcomm’s 8CX, which looked to give desktop-class processing performance in ten watt thermal envelopes. And in September we had a high-level overview of “Apple Silicon”. This overview was based […]